I came across Telnic courtesy of a posting on September 8, 2008 by Jon Udell entitled Annotating DNS with personal information. Thanks, Jon.
Telnic, a UK-based company, is a sponsored top-level domain (sTLD) that, ipso facto, has been authorized by the Internet Corporation for Assigned Names and Numbers (ICANN), which operates the Internet Assigned Numbers Authority (IANA) and is in charge of maintaining the DNS root zone.
Overall, IANA currently distinguishes the following groups of top-level domains:
The term
sponsored top-level domain is derived from the fact that these domains are based on
theme concepts proposed by private agencies or organizations that establish and enforce rules restricting the eligibility of registrants to use the TLD.
As quoted from the
New sTLD RFP Application filed by Telnic in 2004 with ICANN:
The .Tel is a text-based naming and navigation sTLD that addresses the unique needs of the fixed-line and wireless Internet-Communications namespace. This namespace covers any form of intercommunications activity (voice, combined voice/data, or messaging) between individuals and/or businesses, which is dependent, in part or whole, on the Internet as the means of transport .... Digits are to be restricted to maintain the integrity of a letters/words based top-level domain and to avoid interference with established or future national and international telephone numbering plans .... This new sTLD will be ... a vehicle that will allow and encourage individuals and corporations to manage a universal identity in this namespace.
Telnic's
raison d'etre is to provide a universal communication identifier. From application filed with ICANN:
End users are finding it increasingly difficult to remember and manage their own and other people's communication identifiers, including:
- home telephone numbers
- mobile telephone numbers
- home fax numbers
- personal email addresses
- pager numbers
- work telephone numbers
- work telephone extension numbers
- work email addresses
- work fax numbers
- instant messaging addresses
- and other contact information
Hence, there is a need for a universal text based communication identifier under which the end user can store all their contact information.
How would .Tel be used by individuals? The following excerpt is also from the ICANN application, or you can just watch the nifty promotional movie clip,
.Tel for Individuals (3m 23s).
Individuals could use their name as a personal "brand" or a universal identity accessible from any Internet-enabled communications device to publish their contact information or other personal data. For example, Adam Smith could develop a personal mini-website that provides general information about himself including his contact information, such as phone numbers, and email addresses. Adam would be able to update and manage this data at will, and Adam's friends, when trying to reach him, could simply check adamsmith.tel to find his most current contact information and connect the call or send a text message.
How would .Tel be used by businesses? Again, the following excerpt is also from the ICANN application, or you can just watch the equally jazzy promotional movie clip,
.Tel for Businesses (4m 10s).
The business market has different needs than the individual market. Businesses are primarily concerned with customer acquisition and retention, ease of client communication, and efficiency of customer management. The .Tel domain has been conceived to meet each of these needs fully. Hertz, for example, could purchase hertz.tel and design a simple and clear navigational system for customers accessing the company via Internet-enabled communications devices. Hertz could segment the customer by geographic location and department and then route the customer to the appropriate call center, which enhances the customer experience and provides the most efficient and cost effective solution for Hertz.
There's another promotional movie clip posted by Telnic entitled
How Do I protect My Data (1m 42s) that I found worth viewing, too. Actually, all of the several promotional movie clips at Telnic are entertaining, jazzy and informative.
The intellectual property behind .Tel is found in
Communication System (US Pending Patent 20080133471) which was filed under PCT procedures by inventors John Burgess et al. in Great Britain on 1 April 2003, and in the U.S. on 1 April 2004. It is represented as being assigned to Telnic Limited. The following is a key drawing and a related excerpt from the pending patent.
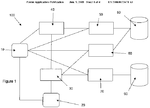 [Original image modified for size and/or readability]FIG. 1 shows a schematic depiction of a system 100 according to the present invention. The system 100 comprises a user 10, a registered user 20, a registrar 30, a registry 40, a search engine 50, a name service provider (NSP) 60, a name navigation service provider (NNSP) 70, an NSP database 80 and an NNSP database 90. It will be readily appreciated that the system will operate with a plurality of both users 10 and registered users 20 but for the sake of simplicity the following discussion will be limited to a single user and registered user. The system enables a user 10, which comprises a mobile communications device (such as a mobile telephone, or wireless-enabled PDA or similar device) to obtain details regarding a registered user that has been registered with the system. Such details may comprise contact data (telephone number(s), fax number, email and/or instant messaging address, etc.) data related to content (internet address(es) for accessing or downloading multimedia resources, e-commerce or m-commerce sites, etc.). It will be understood that many different types of data may be provided. The system has a number of similarities with the existing domain name server (DNS) system. A DNS will receive a request containing an alphanumeric address and will return the IP address associated with that alphanumeric address to a client application so that a communication session may be initiated, using, for example, the ftp or http protocols. In the present invention, a database query will be run in response to a request from a client application (this is similar to a DNS look-up) and an address is returned to the client application which can be used to access the desired data. This similarity enables DNS infrastructure to be used in the implementation of the present invention.
[Original image modified for size and/or readability]FIG. 1 shows a schematic depiction of a system 100 according to the present invention. The system 100 comprises a user 10, a registered user 20, a registrar 30, a registry 40, a search engine 50, a name service provider (NSP) 60, a name navigation service provider (NNSP) 70, an NSP database 80 and an NNSP database 90. It will be readily appreciated that the system will operate with a plurality of both users 10 and registered users 20 but for the sake of simplicity the following discussion will be limited to a single user and registered user. The system enables a user 10, which comprises a mobile communications device (such as a mobile telephone, or wireless-enabled PDA or similar device) to obtain details regarding a registered user that has been registered with the system. Such details may comprise contact data (telephone number(s), fax number, email and/or instant messaging address, etc.) data related to content (internet address(es) for accessing or downloading multimedia resources, e-commerce or m-commerce sites, etc.). It will be understood that many different types of data may be provided. The system has a number of similarities with the existing domain name server (DNS) system. A DNS will receive a request containing an alphanumeric address and will return the IP address associated with that alphanumeric address to a client application so that a communication session may be initiated, using, for example, the ftp or http protocols. In the present invention, a database query will be run in response to a request from a client application (this is similar to a DNS look-up) and an address is returned to the client application which can be used to access the desired data. This similarity enables DNS infrastructure to be used in the implementation of the present invention.
What Telnic is doing is highly innovative from a marketing standpoint. Especially when you consider the hoops they have no doubt had to jump through in getting approval from the bureaucratic body of personalities, standards and procedures that is ICANN. I applaud them for hanging in there and bringing this service to the marketplace.
But it's little difficult to understand how Telnic's patent is innovative from the standpoint of its intellectual property (IP). The strength of what Telnic is doing is strongly tied to mimicking the DNS system, which, again, no doubt served Telnic well in receiving approval from ICANN. Moreover, in the excerpt above the inventors admit that "[t]he system has a number of similarities with the existing domain name server (DNS) system." Further evidence of this lack of IP innovativeness may be surmised from the status of Telnic's EU patent application which was withdrawn in 2007 because "[the] reply to [an] examination report [was] not received in time". That commonly means that the applicant didn't think it was worth pursuing - for whatever reason - and so abandoned the application. See the history to
Communication System (Publication No. EP1609292).
To place all of the above in a broader perspective, while Telnic has taken the text-based, DNS approach to a virtual calling card system, Microsoft has taken a perhaps more object-oriented approach outside of ICANN's DNS jurisdiction for achieving a similar end with its "server-based card exchange". You can see this in comparing Telnic's IP with the summary of Microsoft's IP that I previously blogged in
US Patent 7,149,977: Virtual calling card system and method. Wouldn't a mashup between the two (i.e., a web application hybrid) be interesting to see?
The following received from Justin Hayward, Communications Director for Telnic Limited, after reviewing the foregoing entry:
From: "Justin Hayward" <[address removed>
Sent: Thursday, September 11, 2008 3:00 PM
To: [addresses removed]
Subject: Re: .Tel: Telnic's DNS Virtual Calling Card System
Steve,
Many thanks for your interest and kind words about .tel.
Regards,
Justin
If you have a minute, Justin has an interesting blog, Retrospective Futureologist, with updates on the launch of .Tel.
 Thursday, May 20, 2010 at 12:49PM
Thursday, May 20, 2010 at 12:49PM 

