Title: Method and system for network marshalling of interface pointers for remote procedure calls (Part I)
Patent Number: US Patent 5,511,197
Issued: April 23, 1996
Filed: November 29, 1993
Parent case: Abandoned. However the subject patent is the parent to US Patent 5,724,588 (Microsoft Corporation) Φ.
Inventor(s): Hill, Richard D. et al.
Assignee: Microsoft Corporation
Distinguished after issuance from: US Patent 6,671,696 (Pardalis Inc.)
Blogger comment(s):
There were 7 prior US patents referenced at issuance, and 1 foreign patent document, none of which are remarkable for the scope and purposes of this blog.
An advanced search at USPTO online on May 9, 2008 for references to this patent using ref/5511197 reveals 176 references. A more refined search reveals US Patent 6,671,696.
Abstract:
A computer method and system for passing a pointer to an interface from a server process to a client process.
Independent claims (as numbered):
1. A method in a computer system network for passing a pointer to an interface of an object from a server process in one node of the network to a client process in another node of the network to enable the client process to invoke function members of the interface, the method comprising the steps of:
within the server process,
instantiating the object, the object having an implementation of the interface, the interface having a function member;
creating an interface stub for receiving a request to invoke the function member of the interface and for invoking the requested function member upon receiving the request;
creating a stub channel for receiving the request to invoke the function member of the interface and for forwarding the request to the created interface stub; and
sending an identifier of the stub channel to the client process via network communications; and
within the client process,
receiving the identifier of the stub channel from the server process;
creating an interface proxy for receiving the request to invoke a function member of the interface and for sending the request to a proxy channel;
obtaining a pointer to the created interface proxy; and
creating the proxy channel for receiving the request from the created interface proxy and sending the request to the stub channel identified by the received identifier,
whereby the client process may use the pointer to the interface proxy to invoke the function member of the interface of the object instantiated within the server process.
7. A method in a computer system for passing a pointer to an interface of an object from a server process to a client process to enable the client process to invoke function members of the interface, the method comprising the steps of:
within the server process,
instantiating the object, the object having a plurality of interfaces, each interface having a function member;
identifying an interface of the object to pass to the client process;
creating a stub for receiving a request to invoke the function member of the identified interface and for invoking the function member upon receiving the request, the stub having an identifier; and
sending the identifier of the stub to the client process; and
within the client process,
receiving the identifier of the stub from the server process;
instantiating a proxy object for receiving requests to invoke a function member of the interface and for sending the request to the identified stub; and
obtaining a pointer to the instantiated proxy object,
whereby the client process may use the pointer to the interface proxy to invoke the function member of the interface of the object instantiated within the server process.
13. A method in a computer system for passing a pointer to an interface of an object from a server process to a client process to enable the client process to invoke function members of the interface, the method comprising the steps of:
within the server process,
instantiating the object, the object having a plurality of interfaces, each interface having a function member, the object further having a marshalling function member for performing object-specific marshalling for a pointer to one of the plurality of interfaces;
identifying an interface of the object to pass to the client process;
invoking the marshalling function member of the object to marshal the identified interface; and
sending to the client process a reference to the object instantiated within the server process and an unmarshal class identifier identifying the class of the proxy object to be instantiated by the client process; and
within the client process,
receiving from the server process the reference to the object instantiated within the server process and the unmarshal class identifier;
instantiating an object of the class identified by the unmarshal class identifier, the object of the class identified by the unmarshal class identifier having an unmarshalling function member;
obtaining a pointer to the object of the class identified by the unmarshal class identifier: and
invoking the unmarshalling function member of the object of the class identified by the unmarshal class identifier using the obtained pointer and passing the reference to the object instantiated within the server proxy, the unmarshalling function member for performing object-specific unmarshalling for the pointer to the identified interface,
whereby the client process may use the pointer to the object of the class identified by the unmarshal class identifier to invoke a function member of the identified interface of the object instantiated within the server process.
19. A method in a computer system of passing a pointer to an object from a server process to a client process to enable the client process to invoke function members of the object, the method comprising the steps of:
within the server process,
instantiating the object;
creating a stub for receiving a request to invoke a function member of the object and for invoking the requested function member upon receiving the request, the stub having an identifier; and
sending an unmarshal class identifier identifying the class of a proxy object to instantiate within the client process and the identifier of the stub to the client process; and
within the client process,
receiving the unmarshal class identifier and the identifier of the stub from the server process;
accessing code to instantiate the proxy object of the class identified by the unmarshal class identifier; and
executing the accessed code, including the substeps of;
instantiating a proxy object of the class identified by the unmarshal class identifier, and
initializing the proxy object to contain a reference to the identified stub so that when the proxy object receives requests to invoke a function member of the object, the proxy object sends the request to the identified stub; and
obtaining a pointer to the instantiated proxy object,
wherein the client process may use the pointer to the proxy object to invoke function members of the object instantiated within the server process.
24. A method in a computer system of passing a pointer to an object from a server process to a client process to enable the client process to invoke function members of the object, the method comprising the steps of:
within the server process,
instantiating the object, the object having a marshalling function member for performing object-specific marshalling for a pointer to the object;
invoking the marshalling function member of the object to marshal the identified interface; and
sending to the client process a reference to the object instantiated within the server process and an unmarshal class identifier identifying the class of a proxy object to instantiate in the client process; and
within the client process,
receiving from the server process the reference to the object instantiated within the server process and the unmarshal class identifier;
accessing code to instantiate the object of the class identified by the unmarshal class identifier;
executing the accessed code to instantiate an object of the class identified by the unmarshal class identifier, the object of the class identified by the unmarshal class identifier having an unmarshalling function member;
obtaining a pointer to the object of the class identified by the unmarshal class identifier; and
invoking the unmarshalling function member of the object of the class identified by the unmarshal class identifier using the obtained pointer and passing the reference to the object instantiated within the server process, the unmarshalling function member for performing object-specific unmarshalling for the pointer to the object,
whereby the client process may use the pointer to the object of the class identified by the unmarshal class identifier to invoke function members of the object instantiated within the server process.
29. A method in a computer system for passing a pointer to an object from a server process to a first client process and from the first client process to a second client process to enable the client process to invoke function members of the object, the method comprising the steps of:
within the server process,
instantiating the object;
creating a stub for receiving a request to invoke a function member of the object and for invoking the requested function member upon receiving the request, the stub having an identifier; and
sending an unmarshal class identifier identifying the class of an object to be instantiated in the first and second client processes and the identifier of the stub to the first client process;
within the first client process,
receiving the unmarshal class identifier and the identifier of the stub from the server process;
accessing code to instantiate a first proxy object of the class identified by the unmarshal class identifier;
executing the accessed code, including the substeps of:
instantiating a first proxy object of the class identified by the unmarshal class identifier and having a marshalling function member to specify that the identifier of the stub is to be sent to the second client process, and
initializing the first proxy object to contain a reference to the identified stub so that when the first proxy object receives requests from the first client process to invoke a function member of the object, the first proxy object sends the request to the identified stub;
obtaining a pointer to the first proxy object;
invoking the marshalling function member of the proxy object; and
sending the unmarshal class identifier and the identifier of the stub to the second client process; and
within the second client process,
receiving the unmarshal class identifier and the identifier of the stub from the first client process;
accessing code to instantiate a second proxy object of the class identified by the unmarshal class identifier;
executing the accessed code, including the substeps of:
instantiating a second a proxy object of the class identified by the unmarshal class identifier, and
initializing the second proxy object to contain a reference to the identified stub so that when the second proxy object receives requests from the second client process to invoke a function member of the object, the second proxy object sends the request to the identified stub; and
obtaining a pointer to the second proxy object,
whereby the first client process may use the pointer to the first proxy object to invoke function members of the object instantiated within the server process and the second client process may use the pointer to the second proxy object to make function members of the object instantiated in the server process.
35. A method in a computer system of passing a pointer to an object of a selected class from a server process to a client process to enable the client process to invoke function members of the object, the method comprising the steps of:
within the server process,
instantiating the object in shared memory that is accessible by the server process and the client process, the instantiated object having a data access function member to access data members of the object;
storing an identifier of the selected class in a message as an unmarshal class identifier;
invoking a marshalling function member of the object instantiated within the server process to store a pointer to data members of the object in the message; and
sending the message to the client process; and
within the client process,
receiving the message from the server process;
retrieving the unmarshal class identifier from the message;
accessing code to instantiate an object of the class identified by the unmarshal class identifier;
executing the accessed code to instantiate an object of the class identified by the unmarshal class identifier, thereby instantiating an object of the selected class, the object of the class identified by the unmarshal class identifier having an unmarshalling function member;
obtaining a pointer to the instantiated object of the class identified by the unmarshal class identifier: and
invoking the unmarshalling function member of the object of the class identified by the unmarshal class identifier, including the substeps of:
retrieving from the message the pointer to data members of the object instantiated within the server process, and
storing in the object of the class identified by the unmarshal class identifier the retrieved pointer to the data members so that the data access function member of the object of the class identified by the unmarshal class identifier can access the data members in shared memory.
42. A method in a computer system of passing a pointer to an immutable object having data members and function members from a server process to a client process, the method comprising the steps of:
within the server process,
instantiating the immutable object;
storing an unmarshal class identifier in a message;
invoking a marshalling function member of the immutable object to store the data members of the object in the message; and
sending the message to the client process; and
within the client process,
receiving the message from the server process;
retrieving the unmarshal class identifier from the message;
accessing code to instantiate an object of the class identified by the unmarshal class identifier;
executing the accessed code to instantiate an object of the class identified by the unmarshal class identifier, the object of the class identified by the unmarshal class identifier having an unmarshalling function member; and
invoking the unmarshalling function member of the object of the class identified by the unmarshal class identifier, including the substeps of:
retrieving the data members from the message, and
storing the retrieved data members in the object of the class identified by the unmarshal class identifier so that the function members of the object of the class identified by the unmarshal class identifier can access the data members of the immutable object.
43. The method of claim 42 wherein the immutable object has a class, and wherein the unmarshal class identifier identifies the class of the immutable object.
44. The method of claim 42 wherein the immutable object has a plurality of interfaces and the pointer to the immutable object is a pointer to one of the interfaces of the immutable object.
49. A method in a computer system for performing a function call from a server process to a function within a client process, the function call having an in parameter that is a pointer to an interface of a real object instantiated within the server process, the interface of the real object having a function member, the method comprising the steps of:
within the server process,
creating a stub for receiving a request invoke the function member;
marshalling an identifier of the stub into a message; and
sending the message to the client process; and
within the client process,
receiving the message from the server process;
unmarshalling the identifier of the stub;
creating a proxy for receiving the request to invoke the function member from the client process and sending it to the stub identified by the unmarshalled identifier;
obtaining a pointer to the created proxy; and
calling the function within the client process, passing the obtained pointer to the created proxy as an in parameter.
50. A method in a computer system for performing a function call from a client process to a function within a server process, the function call having an out parameter that is a pointer to an interface of a real object instantiated within the server process, the interface of the real object having a function member, the method comprising the steps of:
within the client process,
initiating a call to the function within the server process;
within the server process,
calling the function within the client process, the function producing the out parameter that is a pointer to the interface of the real object;
creating a stub for receiving a request invoke the function member;
marshalling an identifier of the stub into a message; and
sending the message to the client process; and
within the client process,
receiving the message from the server process;
unmarshalling the identifier of the stub;
creating a proxy for receiving the request to invoke the function member from the client process and sending it to the stub identified by the unmarshalled identifier;
obtaining a pointer to the created proxy; and
returning the obtained pointer to the created proxy as an out parameter of the function call initiated within the client process.
Key Drawing(s):
"FIG. 13 [below] is a block diagram illustrating custom marshalling with shared memory. In certain situations, an object may store its data members in memory that is shared across processes to avoid the overhead of remote procedure calling to access the data members. In FIG. 13, the data 1302 for cell object 1301 is stored in shared memory. Cell object 1303 is created when a pointer to cell object 1301 is marshalled and sent from process P1 to process P2. The custom methods of the IMarshal interface for a cell object are implemented by the following pseudocode.
void IMarshal::MarshalInterface (pstm, iid, pInterface, DestContext)
{ if(DestContext = Shared) then
{ Marshal (pstm, address of data);}
else
{ MakeStub ("Cell", iid, pInterface, &MessageAddress);
Marshal (pstm, MessageAddress)};
}
void IMarshal::GetUnmarshalClass (iid, pInterface, DestContext, cid)
{ if (DestContext = Shared)
{cid = "Cell"}
else
{cid = "CellProxy"}
}
void IMarshal::UnMarshalInterface (pstm, iid, pInterface);
{ UnMarshal (pstm, address of data);
initialize object to point to shared data
}
The parameter DestContext of the method IMarshal::MarshalInterface indicates whether the data of the cell object is stored in shared memory. If the data is not stored in shared memory, then the equivalent of the standard marshalling is performed. If, however, the data is stored in shared memory, then the address of the shared data is marshalled into the message. The method IMarshal::GetUnmarshalClass determines the unmarshal class based on whether the data is in shared memory. If the data is not in shared memory, then the CellProxy class is the unmarshal class. If the data is in shared memory, then the Cell class is the unmarshal class. The unmarshal class and address of the shared data are sent to process P2. After process P2 instantiates the cell object 1303, the process P2 invokes the custom method IMarshal::UnMarshalInterface, which unmarshals the address of the shared data and initializes the object to point to the data."

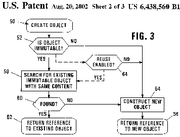
[Original image modified for size and/or readability]"Custom marshalling can be used to provide more efficient access to immutable objects. An
immutable object is an object whose data members (state) cannot be changed. When an interface pointer to an
immutable object is passed from one process to another, custom marshalling can be used to make a copy of the object in the other process. Thus, when the other process accesses the object, it accesses the local copy and no interprocess communication is needed. To allow copying of immutable objects, the methods of the IMarshal interface of the immutable objects are implemented in the following way. In a preferred embodiment, the method IMarshal::GetUnMarshallClass specifies that the unmarshal class is the same class as the class of the
immutable object. This ensures that the same type of object is instantiated by the other process. The method IMarshal::MarshalInterface stores the data members of the
immutable object into a message for passing to the other process. The method IMarshal::MarshalInterface creates no stub. When the other process receives the message, the other process creates an object of the class of the
immutable object. The method IMarshal::UnMarshalInterface then retrieves the data members from the message and initializes the newly-created object. The other process can then access the
immutable object."
 Monday, April 28, 2008 at 3:30AM
Monday, April 28, 2008 at 3:30AM