US Patent 5,220,657: Updating local copy of shared data in a collaborative system (Xerox Corporation)
 Monday, April 21, 2008 at 3:00AM
Monday, April 21, 2008 at 3:00AM Title: Updating local copy of shared data in a collaborative system
Patent Number: US Patent 5,220,657
Issued: June 15, 1993
Filed: April 15, 1991
Parent case: This is a division of an application filed Dec. 2, 1987, now US Pat. No. 5,008,853 (Xerox Corporation). Pursuant to 35 U.S.C. § 154(c)(1), the Xerox 657 patent grant likely expired Dec. 2, 2007.
Inventor(s): Bly, Sara A., et al.
Assignee: Xerox Corporation
Referenced at issuance: US Pat. No. 5,008,853 (Xerox Corporation) and US Patent 5,107,443 (Xerox Corporation)
Distinguished after issuance from: Australian Patent 2002323103 (a foreign filing of US Patent 6,671,696 - Pardalis Inc.), US Patent 6,088,702 (Plantz, Scott H. et al), US Patent 6,240,414 (eiSolutions, Inc.) and US Patent 6,573,907 (Obvious Technology).
Blogger comment(s):
There were 17 references to prior patents at issuance, including US Pat. No. 5,008,853 and US Patent 5,107,443. The remaining 15 references are unremarkable for the scope and purposes of this blog.
An advanced search at USPTO online on May 9, 2008 for distinguishing references to this patent after its issuance using ref/5220657 reveals 242 references. A more refined search reveals US Patent 6,088,702, US Patent 6,240,414, and US Patent 6,573,907.
I have also blogged a comment on this patent in The Roots of Common Point Authoring (CPA).
Structured Data Objects: US Patent 6,088,702 commenting on US Patent 5,220,657 Φ
Abstract:
A multi-user collaborative system in which the contents as well as the current status of other user activity of a shared structured data object representing one or more related structured data objects in the form of data entries can be
concurrently accessed by different users respectively at different workstations connected to a common link.
Independent claims (as numbered):
1. A method for operating a collaborative system that includes a plurality of workstations each having a respective display, a respective user input device, and a respective local memory the collaborative system further including storage means for storing shared data; each of the workstations being connected for accessing the shared data stored by the storage means to retrieve the shared data for storage in the respective local memory and for presentation on the respective display; the method comprising steps of:
receiving from the respective user input device of a first one of the workstations a signal requesting an operation affecting the shared data; and
in response to the signal requesting the operation, performing the following acts substeps of:
locking the shared data stored by the storage means to prevent other operations affecting the shared data;
determining whether an up-to-date copy of the affected shared data is stored in the respective local memory of the first workstation;
if an up-to-date copy of the affected shared data is not stored in the respective local memory of the first workstation, storing an up-to-date copy of the affected shared data in the respective local memory of the first workstation;
performing the requested operation by making a change in the up-to-date copy of the affected shared data stored in the respective local memory of the first workstation;
updating the shared data stored by the storage means to include the change made by performing the requested operation; and
unlocking the shared data stored by the storage means after the shared data stored by the storage means is updated.
Key Drawing(s):
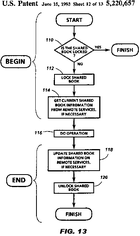
[Original image modified for size and/or readability]"In FIG. 13 there is shown a flowchart which represents the basic transaction occurring during each instance of a shared book operation, i.e. upon user invoked operational commands on shared book 40, wherein such an operation has a requirement or need for current shared book information to properly implement the operation. The transaction of FIG. 13 is carried out to completion from START to FINISH with performance of the invoked "Do Operation" at 116. The transaction of FIG. 13 can be divided, for convenience, into a BEGIN portion and an END portion. The BEGIN portion updates the local copy of shared book information, if necessary. The END portion updates the remote instance of a shared book data file, if necessary, by copying data from workstation 14 to the remote files services. Encompassing these updating functions is the locking and unlocking of the shared book's lock. The BEGIN portion is represented by functions 110, 112 and 114 and the END portion is represented by the functions 118 and 120. In this connection, the implementation for shared books provides arbitration of access to the remote shared book data by using a lock on the shared book. The lock is implemented by the database service and is available over the network. In this manner, any user invoked operation that requires up-to-date shared book data, or could possibly effect data changes, such as opening a shared book 40, opening an entry 44, opening the shared book property sheet 50 or opening an Entry Details property sheet 60, locking a particular entry 44, copying a shared book entry 44 to desktop 32 or copying an entry from desktop 32 back into shared book 40, causes the implementation to acquire or attempt to acquire a lock on the shared book. If successful, the command is allowed to proceed and the lock is held on the shared book for the duration of the execution of the command, after which the shared book lock is released. Otherwise, the user is informed that the shared book is currently in use and displays the name of the other user that presently has the shared book locked."
"Locks are specified for the shared book per se or for an entry or entries. The former control is invisible to the user and the latter control is invoked by the user and is visible to all users in their user interface representation. The former provides for consistent and continuous serialized updating of the shared book representation while the latter gives a user exclusive right over an entry, usually for the purpose of entry modification. It should be realized that the shared book is locked only during execution of an operation command and the lock, therefore, is usually "short living", i.e. milliseconds or seconds or minutes, whereas entry locking occurs manually by a user and will remain indefinitely or at least until invoking of a "Save" command on an entry or explicitly cancelling the lock and, therefore, is "long living", i.e. minutes, days or even weeks. The purpose of the shared book lock is to maintain consistency in updating information in the relaxed WYSIWIS representation about a shared book without processing further updating information from another shared book implementation so that updates to a shared book's data file are serialized by transparently acquiring its lock. Once the lock is released, another user instance is free to acquire the shared book lock via the next user invoked operation command."
"Upon a user invoked operation command, the implementation will conduct a transaction with the remote database service to determine if the shared book is locked, as indicated at decision box 110. If the shared book data file is locked, the task is finished, i.e. aborted, and the user is encouraged to try again. If the shared book data file is not locked, then the shared book is locked, as indicated by box 112. Next, the current shared book information is obtained from the shared book data file, if necessary, i.e. the information, as updated, pertaining to the current list of entries of the shared book and the fields of records pertaining to shared book window 42, the shared book property sheet 50B and each shared book entry property sheet 60B. This function is represented by box 114 in FIG. 13. After information updating of the local instance of the shared book user interface representation, the task originally invoked by the user is processed, as represented by the "Do Operation" of box 116. This task, that will invoke the transaction of FIG. 13, will be an operation at the entry level, such as, opening an entry, copying an entry, opening an entry Details property sheet 60B, locking an entry, paginating one or more entries or printing one or more entries, on the shared book. There are also some operations relative to the shared book entity per se, such as, opening of a shared book icon 40, opening the shared book property sheet 50B, copying an entry into or out of the shared book, or paginating the shared book or copying the shared book to the printer icon, that will invoke the transaction of FIG. 13."
"The next function to occur in the transaction of FIG. 13 is an updating of shared book information, relative to the local instance, to the remote file service, i.e. to the remote shared book data and database files. This is represented by box 118 in FIG. 13. Thus, any local changes to information relating to the shared book 40, for example, addition of a new entry 44C to a local instance of shared book 40 or invoking a "save" command on an entry 44, will be updated to the remote shared book, after which the shared book lock is removed, as indicated at box 120. The transaction is thus completed or FINISH."
