A User-Centric Identity Metasystem
 Friday, August 21, 2009 at 3:34AM
Friday, August 21, 2009 at 3:34AM Introduction to A User-Centric Identity Metasystem -
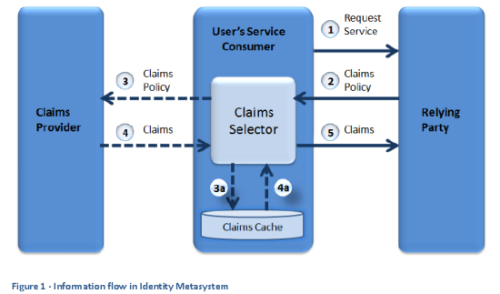
This paper proposes a framework for protecting privacy and avoiding the unnecessary propagation of identity information while facilitating exchange of specific information needed by Internet systems to personalize and control access to services. It also sets out factors to be taken into consideration when deciding where the standardization of such a framework should be brought about. Information systems that co-operate to originate, control and consume identity information have been called identity systems. The evolution of the Internet requires increased interoperability of these systems. Such interoperability demands an abstract model that encompasses the characteristics of all co-operating identity systems. We call this abstract model the Identity Metasystem. Describing, designing, deploying and managing identity systems in accordance with this model will facilitate the interworking of identity components:
- from different manufacturers;
- under different managements;
- of different levels of complexity;
- based on different protocols ;
- employing different syntaxes;
- conveying different semantics; and
- of different ages.
Editor's note ...
With this paper, Kim Cameron, Chief Identity Officer, Microsoft, is seeking to extend Microsoft's Information Cards with 'minimum disclosures' (that is, claims granularly derived from Information Cards). See also Roger Dean interviews Kim Cameron, Chief Msft Identity Architect.
Windows CardSpace (aka Microsoft Information Cards), part of the .NET stack, is Microsoft's client software for the Identity Metasystem, an interoperable architecture for digital identity that enables people to have and employ a collection of digital identities based on multiple underlying technologies, implementations, and providers. When an Information Card-enabled application or website wishes to obtain information about the user, the application or website requests the publication of a particular set of claims authored by the user. The CardSpace user interface then appears, switching the display to the CardSpace service, which displays the user's registered identities. The user selects their InfoCard to verify their identity. See Identity Selector Interoperability Profile V1.0, Microsoft Corporation (April, 2007). See also US Patent 7,149,977: Virtual calling card system and method.
Microsoft's CardSpace is now officially being marketed in the context of the 'Geneva Framework', a Claims Based Access Platform. See also The United Federation of Cloud Providers.
I'm filing A User-Centric Identity Metasystem as a library reference to this blog.

Reader Comments